This feature is currently in Beta. Contact your Customer Success Manager for latest updates on this feature.
This document provides technical guidance for the configuration to send Microsoft Teams based phishing simulations within your organization. These simulations use a “bad actor” lightweight Microsoft 365 account that is given access to Microsoft Teams for the sole purpose of sending simulation messages to “colleagues”. These messages are sent for the sole purpose of training employees to better detect phishing attacks via means other than email.
Microsoft Teams based simulations outline a real-life scenario of an employee who has had their corporate credentials or their device compromized – both are viable outcomes from a sophisticated phishing attack on an employee, or their company.
Prerequisites
The following are prerequisites to successfully launch Teams Phishing Simulations in your organization.
- A Microsoft 365 User License must be available, providing access to Microsoft Teams, for every simulation “bad actor” user account created. The most cost-effective option may be a Microsoft 365 F1 license.
- Microsoft Entra ID Security Defaults must not be enabled in your organization. This is to allow simulation “bad actor” users to have Multi-Factor Authentication (MFA) switched off.
Setup
1. Synchronize Entra ID user ObjectID‘s with OutThink
The first step is to ensure that all users in your organization have Entra ID Object Identifiers synchronized with the OutThink System. These ObjectId’s are used by Microsoft to uniquely identify users within Microsoft Teams, and are a requirement to send Microsoft Teams messages.
Synchronization of ObjectId’s can be achieved in either of the following ways:
- Setup SCIM API integration with your Entra ID (formerly Azure AD). This is explained in detail here.
- Alternatively, for customers synchronizing users using CSV files (manual uploads or SFTP import), User ObjectIds will need to be exported from your Entra ID and included as an additional import field in User CSV import files.
2. Install Eva by OutThink Teams App
To interact with your users via Microsoft Teams, and to grant the required permissions to send chat messages, it is first important to install the Eva by OutThink verified Microsoft Teams app within your Microsoft Teams environment.
It is important to understand that the Eva Application will not be sending the Teams Simulation messages directly, but may be used for proactive follow up encouragement via Teams nudges. The Eva by OutThink Teams App is the launchpad for all interaction with Microsoft Teams and is therefore required to carry out Teams-based Simulation exercises.
Installation instructions are detailed here.
3. Create Microsoft 365 “Bad Actor” account
For assistance with the below steps, follow Microsoft help guidance here.
The user account that you create here does not need to be permanent. You can create the account immediately before the phishing simulation campaign is launched, and delete it afterwards.
Alternatively, keeping the account for longer periods means that it can be re-used across multiple campaigns in the future. Your strategy here is up to you.
- Sign in to the Microsoft 365 Admin Center with an account in the desired tenant with the appropriate administrative rights.
- In the left-side menu, expand the Active Users tab, then Add a User.
- The name given to this user will be instantly visible in Microsoft Teams for any user receiving the simulated attack. The example below uses “Marie Sandoza”, but you can choose any name you wish. Select the name wisely to maximize impact of the simulation.
- Select an appropriate unique email address, and record this. You will need this later.
- Set a complex password, and record this securely. You will need it later.
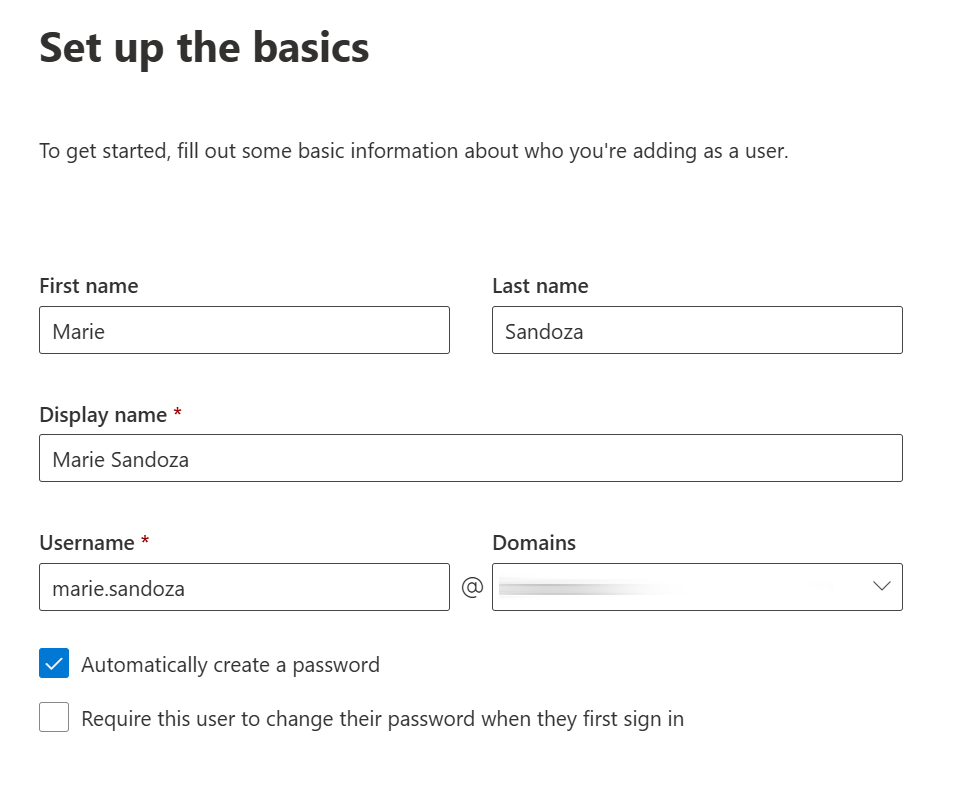
- Click Next.
Setting License & Properties
- Grant the new user an appropriate license that grants access to Microsoft Teams.
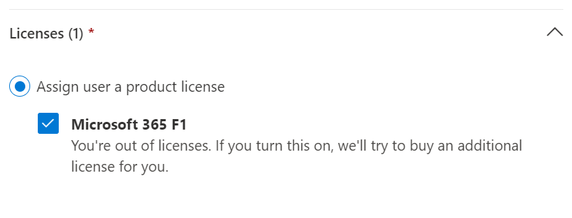
- Click Next.
- Complete the creation of the user by setting appropriate properties. You may wish to segregate this user into a special organization unit, department or division to ensure it is treated seperately from your operational organization.
- Click Next followed by Finish Adding.
Finding Bad Actor User’s Object ID
The new user just created has a unique Object ID in your Entra ID Directory.
We need to find and record this identifier as it will be needed in the final step of the configuration.
- Navigate to the Microsoft 365 Admin Center with an account in the desired tenant with the appropriate administrative rights.
- In the left-side menu, expand the All Admin Centers section at the bottom and then select the Microsoft Entra option to launch the admin console in a new browser window.
- Select Users > All Users on the left menu.
- Browse to or search for the new user, then select the account name to view the user account’s profile information.
- The Object ID is located in the Overview section, under Basic Info. Record this value.
4. Disable Multi-Factor Authentication (MFA)
To send Teams messages seamlessly, we need to disable MFA for this user. Whilst it may be possible to use a user account that has had security information registration deferred, the recommendation is to permanently disable MFA on this user account.
For most Enterprise customers with an Entra ID Premium P1 or P2 license, disabling MFA for a single user can be achieved through an exception in your Conditional Access Policies.
Refer to your own policies and exclude this user from any relevant MFA-based policy. For assistance, contact your Information Security or IT Team.
The following instructions are provided for reference only and may not be appropriate in your organization.
- Sign-in to Microsoft Entra admin center with an account in the desired tenant with the appropriate administrative rights.
- Navigate to the Protection drop-down box and select the Conditional Access option.
- Click on + Create new policy to create a new policy and give a suitable name for your policy.
- Under Assignments, add All users in the Include section and select the new “bad actor” user account in the Exclude section.
- Under the Access controls section, grant access by selecting Require multifactor authentication from the Grant blade, and then click Select to confirm your choice.
- Finally, enable the policy to On mode and click Create.
Please remember that the existence of the “bad actor” user account and any MFA exceptions can be temporary for the life of the Teams phishing simulation, and removed subsequently.
5. Command Center Configuration
The final stage of configuration is to provide the details of your new “bad actor” account in the Command Center, so that it can be used to send simulated phishing messages.
Login to the Command Center, and navigate to Settings. Ensure the correct organization is selected on the left, and head to Integrations > MS Teams Simulations. Ensure the feature is Enabled and then click Settings.
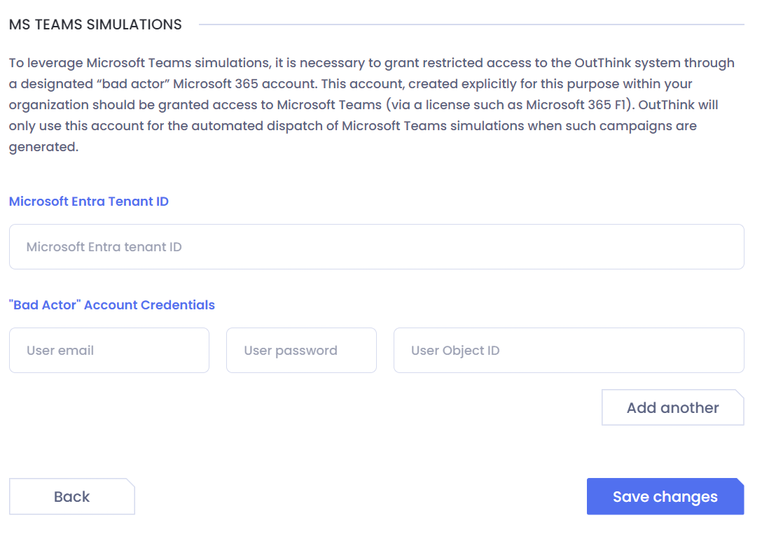
The following information should be supplied here:
Microsoft Entra tenant ID – The unique identifier of your Entra tenant. Refer here for assistance finding this identifier.
User email – The email address of the user account you just created in the M365 Admin Center.
User password – The password of the user saved from the previous section.
User Azure ID – The Object ID of the user in your Entra ID, as saved from the previous section.
If you wish, you can add further bad actor accounts on this screen. Where more than one account exists, the OutThink platform will select a random account to use for each simulation that you create.
When done, click Save changes.
Testing
Before sending any large-scale simulations, it is important to test the integration. This can be done by running a Microsoft Teams Phishing Simulation to a group of a few users from the OutThink Command Center.
Please follow the steps in our help guide, or contact your OutThink Customer Success representative for assistance.
Disclaimer
Your use of Microsoft 365 will be bound by terms of use accepted by your organization during sign-up. OutThink accept no responsibility whatsoever for any use of such accounts which may contravene terms and conditions which your organization has previously accepted. It is your responsibility for ensuring that use of Microsoft 365 for the purposes stated in this document, including sending simulated phishing attacks via Microsoft Teams, adhere to any local or regional terms outlined by Microsoft and accepted by you.
Banner photo by Mika Baumeister
Was this helpful?
4 / 0