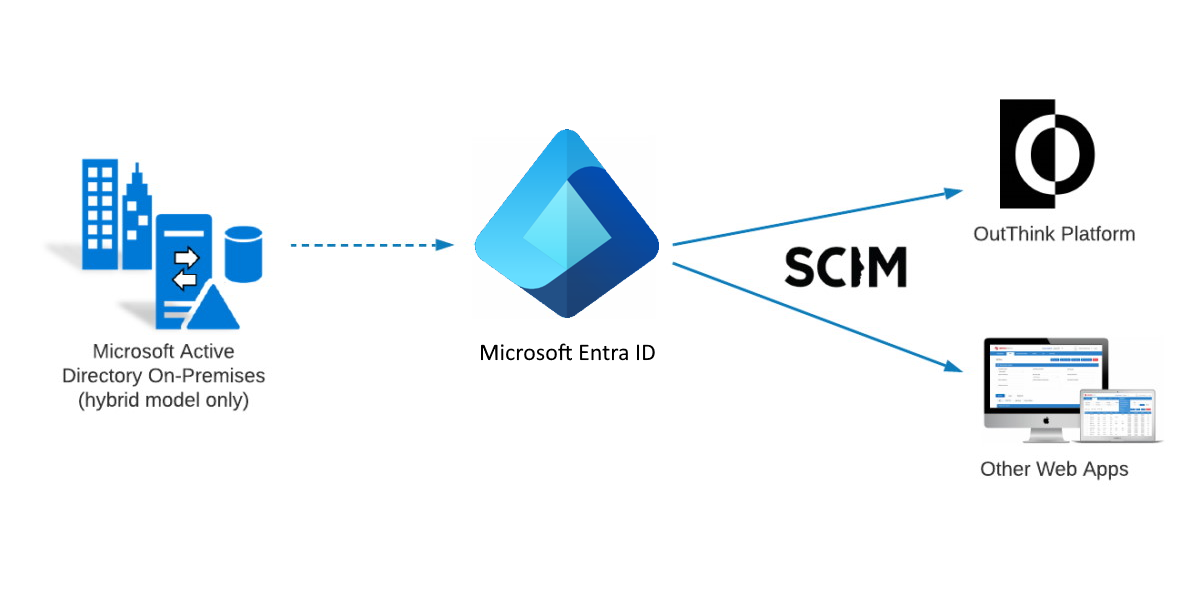
For customers using Microsoft Entra ID (Azure AD) as their Identity Provider, this section serves as a tutorial to setup the required synchronization with an Organization on the OutThink platform.
Creating a new enterprise application in Entra ID (Azure AD)
If necessary, the following procedure can be repeated any number of times to synchronize different user populations with different organizations or divisions, as modelled for your company in the OutThink system.
- Sign in to your Entra ID as an Administrator, go to Enterprise applications then select the + New Application option.
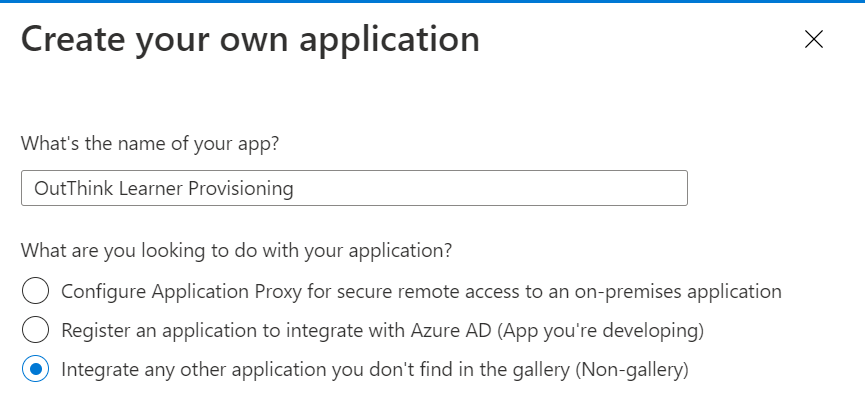
- From the top menu, select Create your own application.
- Use a name such as “OutThink End-User Provisioning” for the application, and select the option Integrate any other application you don’t find in the galley. Click Create.
Assigning users to the application
- On the new enterprise app’s left panel, under Manage, click the Users and groups option.
- Use the Add User/Group option to assign the end-users that you wish to provision to the OutThink platform.
Please note you should only assign human user accounts to the application for synchronisation, i.e. ignore administrator, service and test accounts. You should also try to avoid assigning any human user that will not take part in any training or simulations. You may need to set up a new user group, possibly a dynamic group (link is for Microsoft documentation).
Provisioning your enterprise application
- On the new enterprise app’s left panel, under Manage, click the Provisioning option, followed by Get Started.
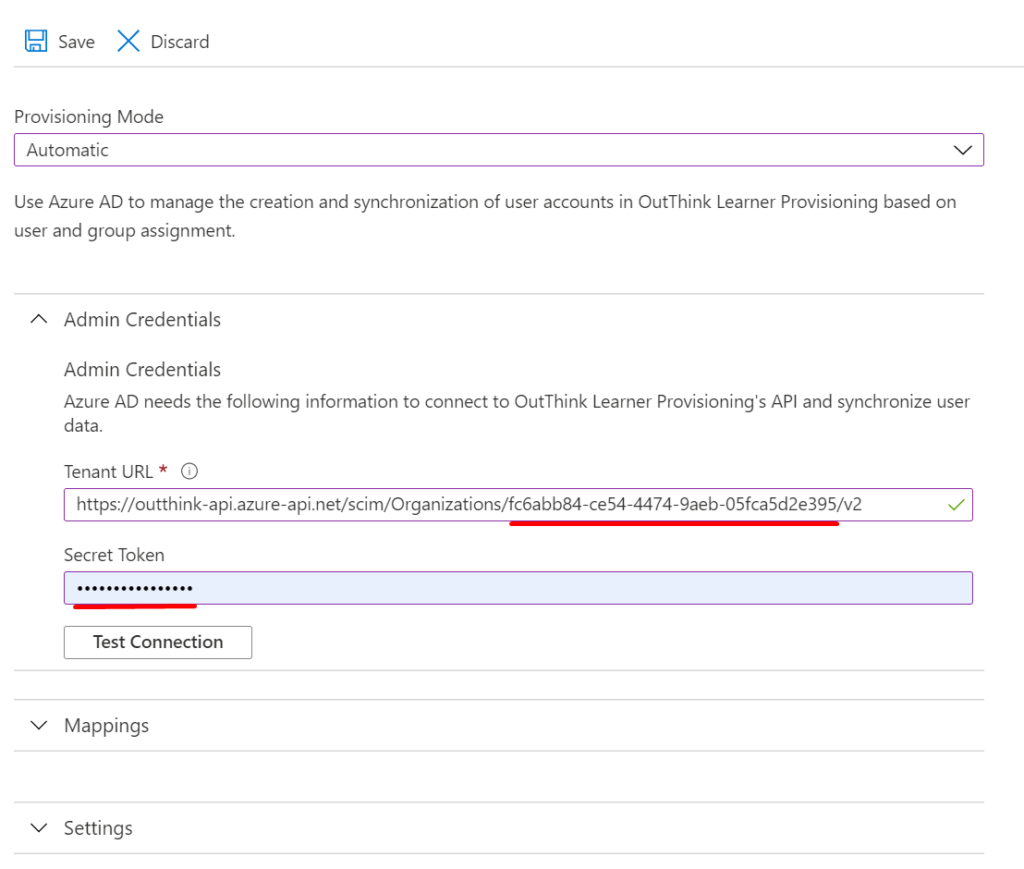
- On the screen that follows, set the Provisioning Mode to Automatic.
- Under the Admin Credentials section, set the Tenant URL to your unique organization URL, as outlined in the Basic API Information in the parent article. Contact OutThink to obtain your unique organization id.
- In the Secret Token field, enter the token corresponding to your organization. Contact OutThink to obtain the token, and once set click Test Connection followed by Save.
Mapping Users
Under the Mappings section, ensure that the Provision Azure Active Directory Users is set Yes.
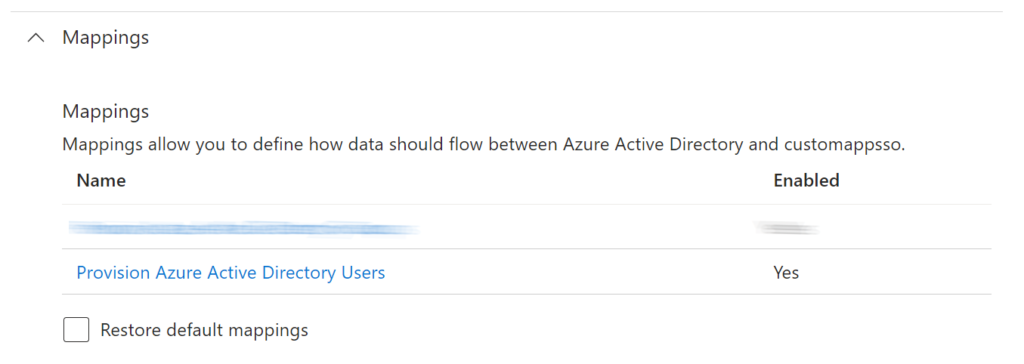
- Click on the hyperlinked text Provision Azure Active Directory Users.
- Adjust your user Attribute mappings so as to include only those attributes of your Azure AD users that you want to synchronize with OutThink. You must delete all unwanted attributes for a successful provisioning to happen.
Click the Save button every time you perform an action within attribute mapping.
OutThink do not require any custom schema attributes to be created, and end-users can be provisioned using attributes defined within both the SCIM core and the SCIM Enterprise User Extension schemas. The information below shows an example set of mappings. Your organization may however wish to setup mappings differently according to your requirements.
| Example Azure AD Source Attribute | Target SCIM Attribute | Mandatory? |
|---|---|---|
| userPrincipalName | userName | Yes |
| Not([IsSoftDeleted]) | active | Yes |
| emails[type eq “work”].value | Yes | |
| objectId | externalId | Yes |
| givenName | name.givenName | Yes |
| surname | name.familyName | Yes |
| country | addresses[type eq “work”].country | No* |
| jobTitle | roles[primary eq “True”].value | No* |
| department | urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:department | No* |
| division | urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:division | No |
| employeeId (or mail) | urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:employeeNumber | No |
| mailNickname (or alternative) | nickName | No |
| preferredLanguage | preferredLanguage | No |
* Whilst not strictly mandatory, these fields are highly recommended. If not provided, available results will be limited.
In particular, note the following:
externalId – Unique global identifier of the user.
This is an unchanging permanent unique identifier for the user, and should typically be mapped to the Azure AD user’s objectId field.
addresses[type eq “work”].country – The User’s country, typically where they reside or perform their work.
If provided, this must be an ISO 3166-1 “Alpha 2” Code, such as “GB”, “US” or “FR”. This is typically mapped to the country field in Azure AD.
urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:employeeNumber – The user’s unique employee number within the organization. This is only used if OutThink is delivering training via your corporate LMS System. In this case, you can map any field which represents the internal unique identifier of users from your LMS. Examples may include employeeId or mail. If in doubt, contact your IT or Learning department.
nickName – The user’s unique name, badge Id, or other identifier, used for identification of the user. This field is optional, but will be required where shop floor or factory based workers require access to the OutThink Training Center (Training Portal), but do not have their own allocated email address. If provided, it should be unique across all users. This can be mapped to any appropriate field in AzureAD, such as mailNickname or otherwise.
preferredLanguage – The user’s native or preferred language.
If provided, this must be a combination of an ISO-639-1 Language Code and an ISO-3166-1 Alpha 2 Country Code. For example, “en-US”, “fr-FR” or “pt-BR”. This is typically mapped to the preferredLanguage field in Azure AD.
Line Managers
Due to Microsoft Entra ID non-conformance to the SCIM specification, ingestion of line managers should now be achieved via a GraphAPI integration. Any mapping of Entra ID manager fields to SCIM field can be removed.
Mapping Groups
If you also wish to synchronize groups from your Azure AD to the OutThink platform, set Provision Azure Active Directory Groups to Yes.
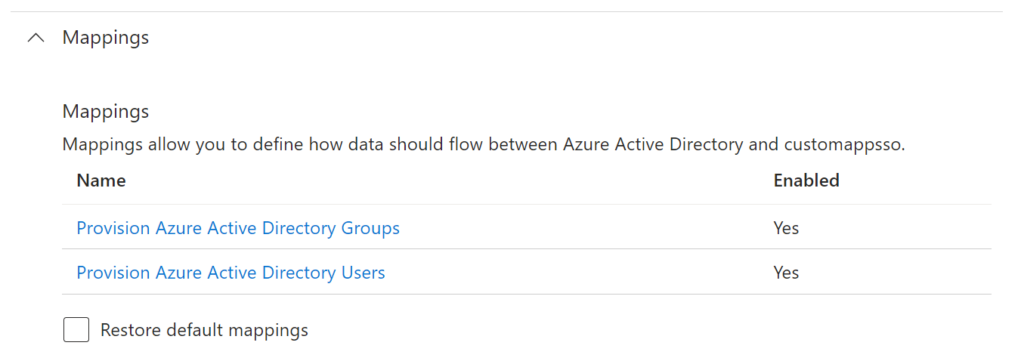
- Click on the hyperlinked text Provision Azure Active Directory Groups.
- Review your user Attribute mappings so as to include the necessary attributes of your Azure AD Groups. These will typically be as follows:
| Example Azure AD Source Attribute | Target SCIM Attribute | Mandatory? |
|---|---|---|
| displayName | displayName | Yes |
| objectId | externalId | No |
| members | members | No |
If you make any changes to the attribute mapping, ensure that you click the Save button.
Testing Provisioning
Once the attribute mapping is complete, you can test provisioning by using the Provision-on-demand option from the Enterprise Application’s Provisioning screen.
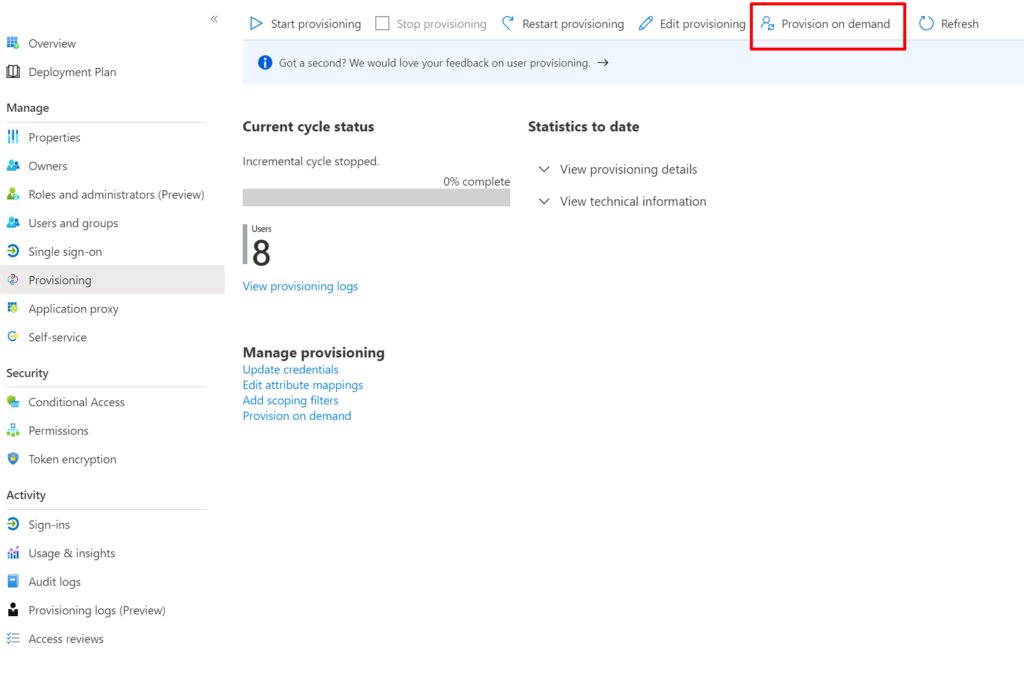
Enter the details of a user who has been assigned to the Enterprise Application, and test provisioning. Any errors or success messages will be immediately displayed. Launch the OutThink Command Centre and review the User Dashboard to determine if the changes have been reflected. Important: It may take several minutes or more for a manually provisioned user to be reflected correctly in the Command Centre.
Enabling Automatic Provisioning
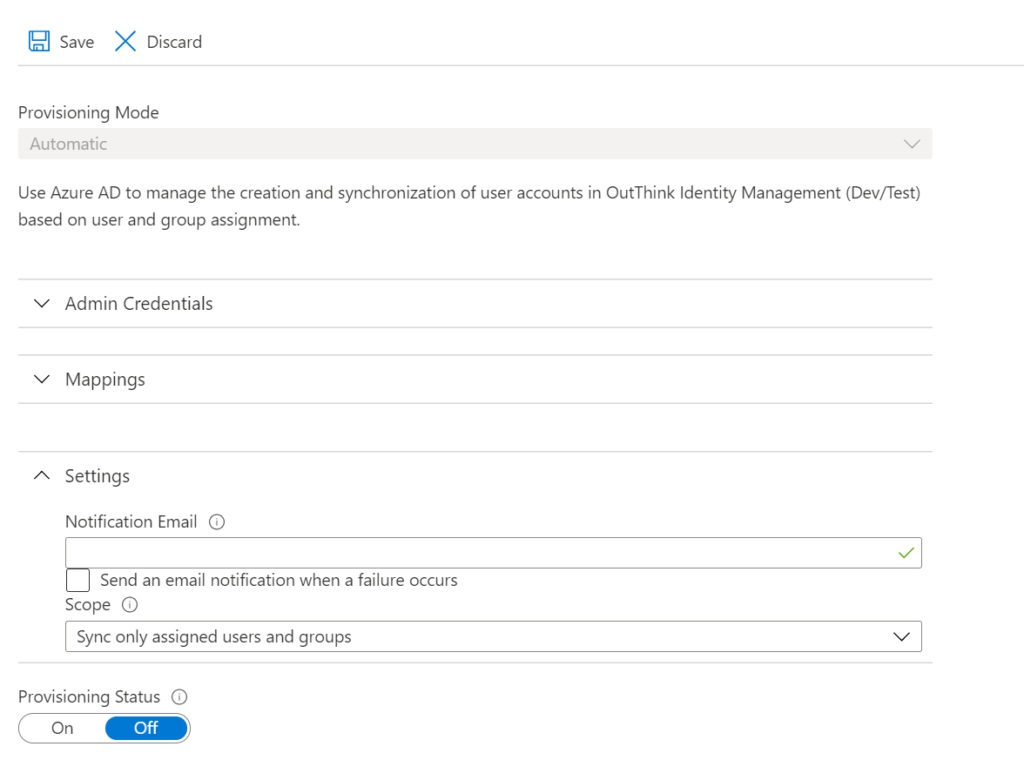
Once you have tested provisioning and are ready to automate the provisioning of end-users, you can switch on automatic provisioning using the Provisioning Status option on the Provisioning page of the Enterprise Application. Under Settings, also ensure that the Scope of the integration is set to Sync only assigned users and groups.
Was this helpful?
8 / 0