This section defines the setup for Single Sign On for Administrators to access the OutThink Command Center. If you wish to enable the SSO option for end-users when accessing their training, refer to the documentation here.
The OutThink Command Center is a secure on-line portal for managing your end-users, training campaigns, attack simulations, and interacting with analytics results and reporting. Only named and trusted administrators should be granted rights of access.
This article describes how to set up a federation with your identity provider (IdP) supporting the OpenID Connect (OIDC) protocol. When you set up the federation, new administrative users of the OutThink platform can use your own IdP-managed organizational account to sign in to the OutThink Command Center. Examples of OIDC Compatible Identity Providers include Microsoft Entra ID, Auth0, Okta, Google and many others.
1. Provide IdP Metadata to OutThink
Please supply the following information from your OIDC-compatible Identity Provider, and send via your Customer Success Manager. OutThink will setup the SSO Federation and inform you when it is complete and ready for testing.
| Setting | Details |
|---|---|
| Issuer URL | The complete URL of the OpenID Provider. |
| Client ID | The client identifier, as registered with the OpenID Provider. |
| Client secret | Client secret is used in conjunction with the Client ID to authenticate the client application against the OpenID Provider. |
| Username mapping | An attribute from your IdP that uniquely identifies a user and can be mapped to the username in OutThink. For example, if you entered ${NameID}, we would use the values of this attribute from your IdP as usernames. Check your IdP docs for the list of attributes. |
| Additional scopes | Scopes are used by an application during authentication to authorize access to a user’s details. Each scope returns a set of user attributes, which are called claims. The default scope required is openid. Add more scopes (comma separated) if needed to obtain the username claim.It is recommended to also add scopes family_name and given_name. |
2. Configure your Identity Provider
You will need to configure your Identity Provider so that it knows how to process authentication requests from OutThink.
Copy the following Redirect URL, and paste at the appropriate configuration screen at your Identity Provider. For details, consult the help or support documentation for your Identity Provider.
For customers with a data hosting location in the United States:
https://auth.outthink.app/oauth2/idpresponse
For all other customers:
https://cc.auth.outthink.io/oauth2/idpresponse
If you are unsure where your data is hosted, contact your Customer Success Manager.
3. Test the configuration
It’s important to now test the configuration. Your Customer Success Manager will provide you with your organization’s unique login hyperlink which you should load into a web browser.
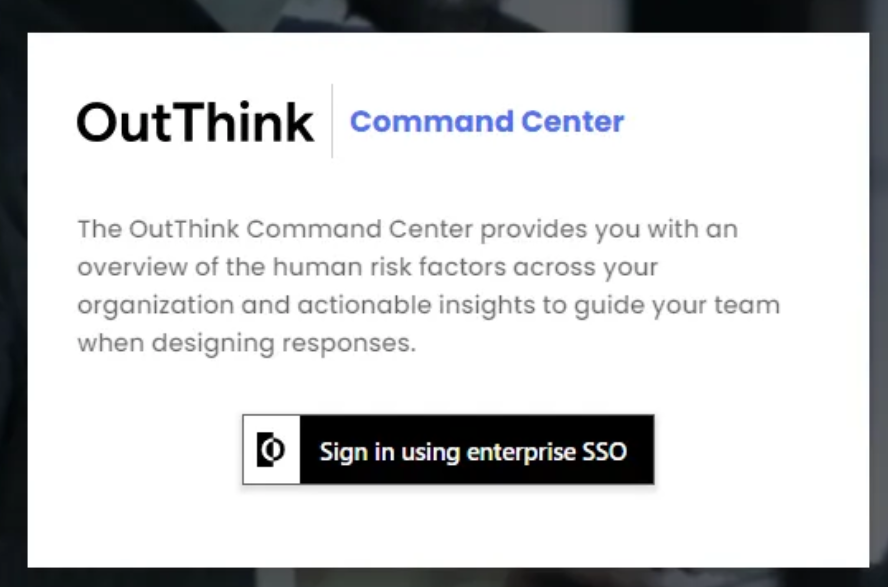
After clicking the Sign In button, you should be redirected to your Identity Provider where you should attempt to sign in with your corporate credentials (note: if you already have an authenticated browser session with your Identity Provider, you may not be asked for your credentials).
You should then be automatically redirected to the OutThink Command Center and be presented with the Command Center Home Page.
Was this helpful?
4 / 0