
This article applies to organizations with Microsoft Defender for Endpoint onboarded devices.
Where a phishing simulation domain is used extensively, it is probable that over time those domains will start to incorrectly appear on security vendors blacklists, and be flagged as a malicious website. Unless the vendor is aware of the ethical use of such domains, this is likely to happen. Microsoft Defender, amongst other providers, will use those blacklists and their own increasingly intelligent algorithms to make determination of whether a given website is safe or malicious. If it is determined that a site is malicious, users clicking phishing simulation links in a phishing simulation email may be prevented from visiting the simulation landing page. Such intervention limits the effectiveness of phishing simulation training.
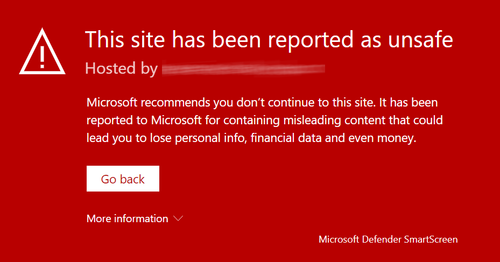
OutThink’s Security Operations Team proactively work with security vendors to ensure that the domains used for phishing simulations do not appear on blacklists, and vendors like Microsoft are informed in advance of the use of such simulation domains. However this process takes time, and it is possible that large scale use of a domain means that it still gets flagged as malicious.
If your users devices are onboarded using either Microsoft Intune or Microsoft Defender for Endpoint, it is recommended to introduce a SmartScreen allowlist to be sure that this feature does not interrupt users when clicking simulation hyperlinks.
Contact your Customer Success Representative to obtain the most recent phishing simulation domains to be whitelisted.
Microsoft Defender for Endpoint
Follow these instructions if you have devices onboarded to Microsoft Defender for Endpoint.
- Navigate to the Defender Portal at https://security.microsoft.com.
- Navigate to Settings on the left side menu, then Endpoints > Advanced Features (direct link – https://security.microsoft.com/securitysettings/endpoints/integration). Ensure that Custom network indicators is enabled.
- Navigate to Rules > Indicators and click on the URLs/Domains header (direct link – https://security.microsoft.com/securitysettings/endpoints/custom_ti_indicators?childviewid=url) .
- Repeat the following for each phishing simulation domain to be added to the allow list.
- Click + Add item.
- Enter the domain to be whitelisted (URL/Domain), and an appropriate Title and Description. Click Next.
- For the Action, choose either Allow or Audit and click Next.
- Confirm the Organizational Scope, click Next.
- Review the summary, and click Submit.
- Once all domains are added, it may take up to 2 hours for the domains to be whitelisted across your organizations devices.
Microsoft Intune
Follow these instructions if you have an Entra ID or hybrid Azure environment and are using Microsoft Intune for Mobile Device Management (MDM). This solution is for Windows devices only.
- Navigate to the Intune Portal at https://intune.microsoft.com.
- Navigate to Devices on the left side menu, then Configuration.
- Click Create > New Policy.
- Select Platform = Windows 10 and later, Profile Type = Templates, and Template Name = Administrative Templates.
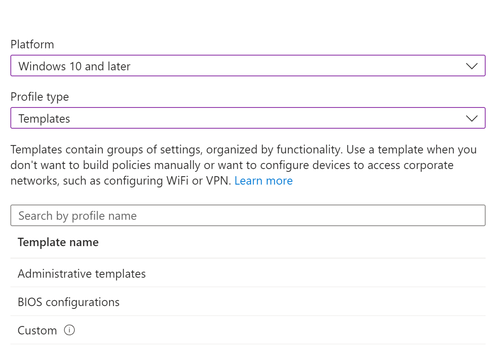
- Click Create at the bottom of the page.
- Enter the Name for your configuration profile and a Description (optional). Click Next.
- In your configuration settings, click Computer Configuration from the side and select Microsoft Edge.
- Scroll down and click SmartScreen Settings.
- Click the setting called Configure the list of domains for which Microsoft Defender SmartScreen won’t trigger warnings.
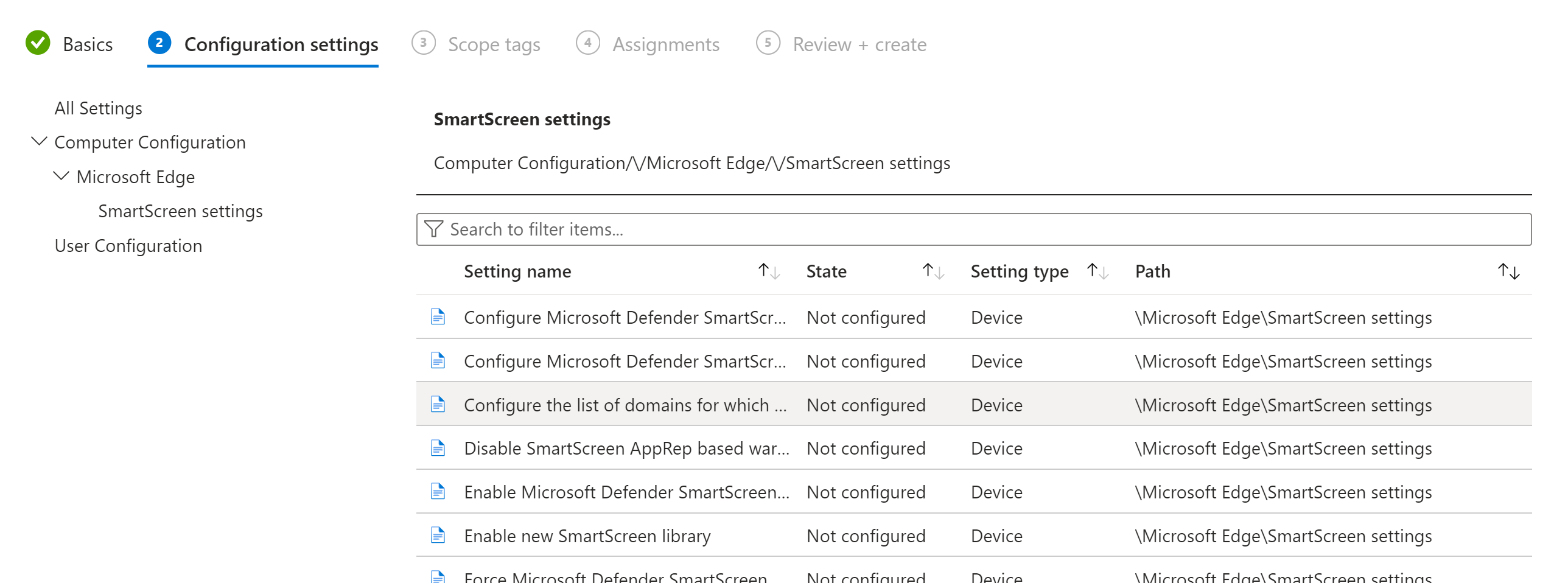
- On the Configure the list of domains… pop out, you will need to configure the following settings:
- Supported on: Microsoft Windows 7 or later > select Enabled radio dial.
- Enter all phishing simulation domains here provided by OutThink, one per line.
- Click OK. This will return you to the SmartScreen Settings page, click Next.
- If applicable, select Scope tags. Click Next.
- In the Assignments screen, click Add all devices.
- Click Next and review your settings.
- Click Create to finalize. This updated profile will be pushed to any device managed by InTune in the next 1-2 hours.
Using Registry Keys (Windows)
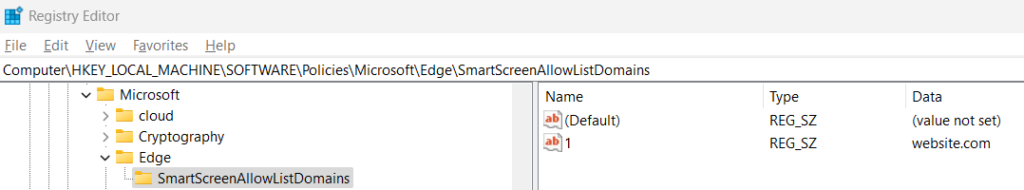
In Windows, you can also set up registry keys for setting the allow list in SmartScreen. Create/check the below key, manually or via deployment:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge\SmartScreenAllowListDomainsCreate new String Value keys (REG_SZ) named “1”, “2”, and so on. The value data is the domain name, e.g. website.com
Microsoft Edge on MacOS
For Intune-managed MacOS devices, however the “.plist” preference file can also be deployed via other MDM solutions.
- Create a new policy in Devices > Configuration (for MacOS, type Templates, name Preference File)
- Configuration Settings – Preference domain name = com.micrisoft.Edge
- Create a text file called “com.microsoft.Edge.plist” with the below text included, replacing “website.com” with the simulation URLs provided. Duplicate the <array> entries to enter more than 1 URL. Upload this file (must be a .plist file extension) to the policy:
<key>SmartScreenAllowListDomains</key>
<array>
<string>service-tech-help.com</string>
</array>- Assign the policy to the relevant groups, or choose “Add all devices”
Was this helpful?
8 / 0