
The OutThink Phishing Reporting Add-In is available for Microsoft Outlook (including Outlook 2016, Outlook 2019 and Outlook for Microsoft 365). This article describes how the add-in can be deployed centrally for your organization.
In all cases OutThink recommend deploying the add-in to a small subset of users before deploying to a larger audience. This allows the process to first be tested, and the add-in features and operational practices to be familiarised.
If your organization is using Microsoft 365 or a hybrid environment, first refer to Microsoft’s article here to determine if your organization supports centralized deployment. If so, follow the first section (“Centralized Deployment”) below.

Add-In Deployment
The first step is to obtain the Add-In manifest file, by downloading it from the OutThink Command Center. Once logged in to the Command Center, navigate to Settings in the top menu.
Ensure the appropriate organization is selected on the left hand side, then click the Integrations menu under the Organization heading. Ensure that the Outlook Reporting PlugIn integration is Enabled, and then click the right arrow icon to expand the settings.
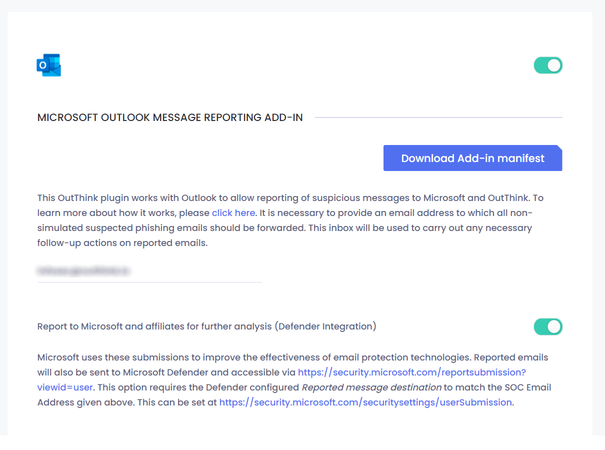
Click the Download Add-in manifest button. Save the downloaded file to your local computer, or to a cloud storage account. You will need it in the following steps.
Centralized Deployment (for Microsoft 365 / Hybrid)
This information has been summarised from the official Microsoft documentation. For more detail, refer to the documentation directly at https://docs.microsoft.com/en-us/microsoft-365/admin/manage/manage-deployment-of-add-ins?view=o365-worldwide
- Sign in to Microsoft 365 Admin Center as an administrator, and go to to Settings > Integrated Apps.
Alternatively navigate directly here via https://admin.microsoft.com/#/Settings/IntegratedApps. - At the top of the page, choose Add-ins.
- Choose Deploy Add-In at the top of the subsequent page.
- Choose Next after reviewing the requirements.
- On the next page, click the Upload custom apps button under the Deploy a custom add-in option.
- When asked how to upload the add-in, select Upload manifest file (.xml) from device.
Select Choose File to locate the manifest file (.xml) you previously downloaded. - Choose Continue after reviewing the add-in details, Privacy Policy, and License Terms.
- On the Assign Users page, choose Everyone, Specific Users/Groups, or Only me. Use the search box to find the users and groups to whom you want to deploy the add-in. For Outlook add-ins, you can also choose the deployment method Fixed, Available, or Optional.
- When finished, choose Deploy. This process may take up to three minutes. Then, finish the walkthrough by pressing Next. You now see your add-in along with other Office apps.
Important: Once deployed, the add-in may not appear on end-users devices for several hours, and in some cases up to 24 hours.
On-Premises Deployment
For on-premises and online environments that do not use the Azure AD identity service, you can deploy Outlook add-ins via the Exchange server.
Outlook add-in deployment requires:
- Microsoft 365, Exchange Online, or Exchange Server 2016** or later.
- Outlook 2016** or later.
To assign add-ins to tenants, you use the Exchange admin center to upload a manifest directly. To assign add-ins to individual users, you must use Exchange PowerShell.
** Important Note
Exchange Server 2016 and Exchange Server 2019 reached end of support with Microsoft on October 14, 2025.

Configuring and testing the Add-In
As mentioned above, it is highly advisable to deploy the add-in to a test group of users first. The add-in should appear in the Office ribbon within the Microsoft Outlook desktop application, or Microsoft Office on the Web (OWA). This only appears when any email is highlighted in the preview pane, or opened in focus.
The OutThink Phishing Reporting Add-In for Outlook should be configured via the settings page in the OutThink Command Centre, as outlined here. Refer to this page for instructions on how to correctly set-up the add-in.
Now for some testing…
Test reporting any random email, to ensure that the suspect email is immediately removed from your inbox, and attached to an email report sent to your SOC Team, Information Security Officer, or other address where the email can be scrutinised and further actions taken.
Next, test sending an attack simulation via the OutThink Command Centre, or via your Customer Success Manager (with our hosted service). When the simulation lands in your inbox, use the phishing reporting feature to report the email. The email should again be removed from your inbox, but this time the campaign analytics and reports will be updated to register that the simulation was successfully reported. In this case the email is not forwarded to your SOC Team.

Remove Outlook’s built-in Report Button
Once the OutThink Phishing Reporting Add-In is successfully installed, configured and working, it is prudent to remove Microsoft’s native Outlook report button. This ensures that users are not confused as to which button to use to report potential phishing attacks.
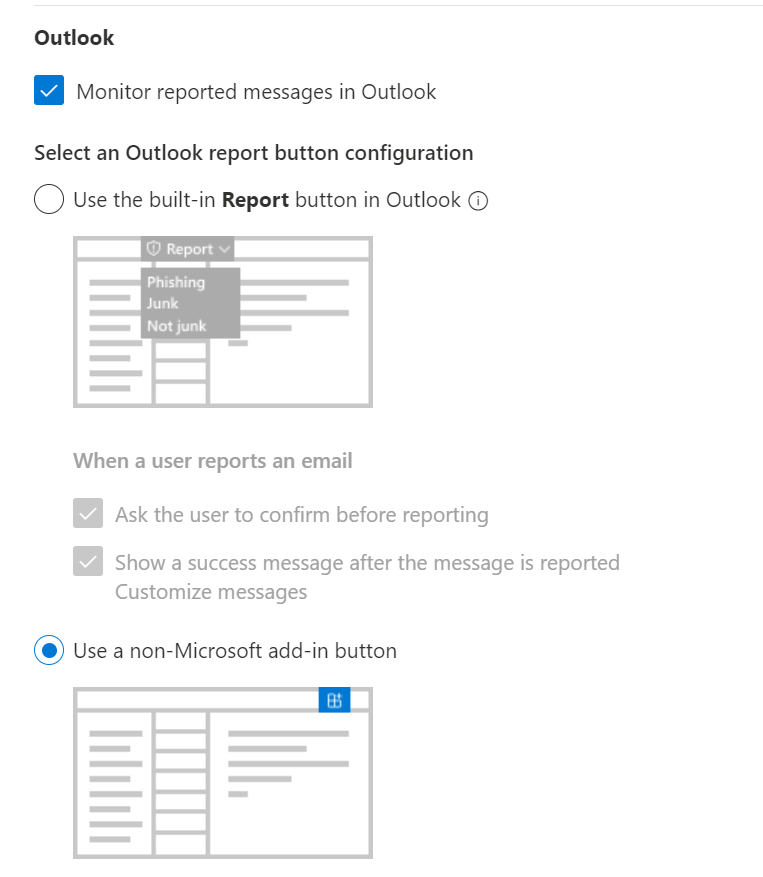
- For Microsoft 365 customers, navigate to the User Reported Settings page of the Email & Collaboration section of the Microsoft 365 Defender portal. This can be accessed directly here.
- Ensure the “Monitor reported messages in Outlook” option is checked, and the “Use a non-Microsoft add-in button” radio button is selected.

Integrate with Microsoft Defender
When users report emails that are not part of an OutThink simulation, the OutThink add-in can be configured to send those suspicious email reports directly to Microsoft Defender. From the Defender Dashboard, IT Administrators can then review all such alerts and take further action as necessary.
For Defender integration to work successfully, both the following sections must be configured.
From Microsoft Defender:
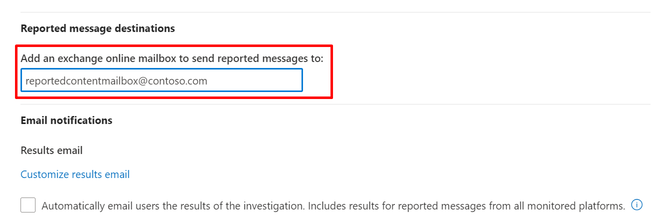
- A SOC Mailbox must be configured in Microsoft Defender’s Advanced Delivery policy. This is outlined here.
Note: The mailbox to be used must have a valid M365 license assigned, and not be a distribution list or alias. - The Defender User Reported Settings option “Reported Message Destinations -> Add an exchange online mailbox to send reported messages to” must be set to your SOC Mailbox email address (as configured above). This setting can be found here.
From the OutThink Command Center:
These option can be found in Settings > Integrations > Outlook Reporting Plugin > Settings.
- The option Forward reported emails to my Information Security Team or SOC must be set to the SOC Mailbox email address, as configured in the previous section.
- The option “Reporting to Microsoft and affiliates for further analysis (Defender Integration)” must be switched ON.
Once these settings are configured, user reported messages should appear in the Microsoft Defender User Reported Dashboard at https://security.microsoft.com/reportsubmission?viewid=user.
Note: alerts can sometimes take up to an hour to appear in the Microsoft Defender Dashboard.
Important:
Microsoft Defender cannot detect reported emails that include additional images or attachments. If you have an email signature system (such as Exclaimer) applying a graphical signature to your corporate emails, it is important to add an exclusion to remove this signature when the email recipient is the SOC Email Address. Contact your email signature provider for details of how to contextually remove the signature in this way.
Placement of Outlook Phishing Reporting Add-in
The placement of the Phishing Reporting Add-In varies across the different formats of Microsoft Outlook.
Please note these are subject to change
- Windows desktop – visible on the Home (mailbox view) and Message (email view) tabs
- Windows desktop (NEW) – accessible by viewing an email, and using the 3-dots menu
- MacOS desktop – accessed via the main toolbar (use 3-dots icon if space shortage)
- Outlook Web – accessible via the Apps menu on an email, alongside Reply/Reply All/Forward
- Outlook for iOS – accessible via the 3-dots menu on an email, beneath the date/time
- Outlook for Android – accessible via the Add-Ins button, beneath folder location text.
Banner photo by Markus Spiske
Was this helpful?
28 / 0